Frequently asked questions
This FAQ is designed to answer your most pressing questions about how Faction works, what makes it different from traditional VPNs and SDNs, and how you can get started. If you’re new to Faction or looking to deepen your understanding, you’re in the right place.
Let’s explore how Faction puts you in control of your network, devices, and data.

StartEngine
Can I Talk to Someone About My Questions?
Absolutely! To get ‘the pitch, ask questions or other information requests about our company, products and the investment opportunity, you can schedule a 15 minute Zoom meeting with Geoff Halstead, Co-Founder and Chief Product Officer here:
What is a Convertible Note
When someone invests what exactly are they getting? A piece of future stock?
What investors are getting is a convertible note is a short-term debt instrument that an investor can convert into equity (ownership) in a company at a later date, typically during a future funding round or exit event, rather than being repaid as a loan. Here is a detailed primer on Convertible Notes:
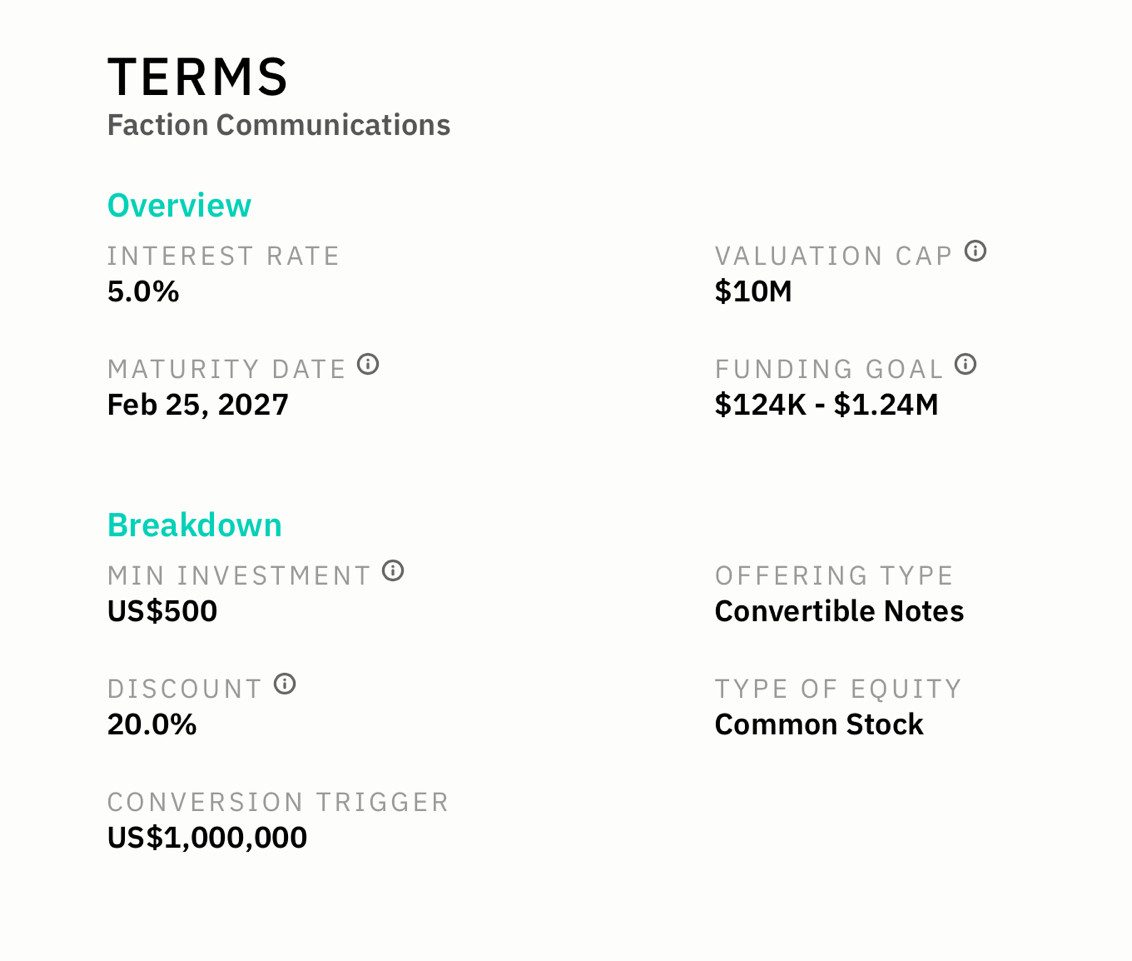
The primary terms are for our Convertible Note on StartEngine are the following:
- 5% interest
- 20% discount on first priced round
- $10M valuation cap
- $1M Conversion Trigger
- 2 year term – expressed as a ‘Maturity Date of Feb. 27, 2027
Interest Rate
Is self explanatory. But most people don’t invest in convertible notes for the interest. It’s a way to buy an equity stake at preferential terms when no valuation can yet be set.
Discount
If Faction Networks did our first ‘priced round’ – either ‘Series A’ or ‘Seed Plus’ – at $10M valuation, then the CN holders would get a discount of 20%. So, they convert – or buy – their shares at $8M valuation while everybody else is paying $10M.
Valuation Cap
Our target for our first priced round valuation is $20M or greater. So, in that scenario, they convert at $10M when everyone else is paying $20M valuation. i.e. Investors would have doubled their money in the valuation.
Conversion Trigger
The conversion trigger is based on a *priced* round, whereas this is a Convertible Note. That’s when we sell shares at a valuation price as described above.
Term
When the note must be paid. If the Trigger event does not happen by the end of the term, the note must be paid – principle + interest. There is always the risk that the company goes out of business, so then you are just a creditor. But at least for scenarios where the company is operating but perhaps growing more slowly, convertible note holders have a decent change of getting paid back. Or they could elect to convert to equity at term.
Summary
This how our convertible note is summarized on StartEngine
I am NOT an accredited investor. Do I need to be?
StartEngine is a great platform and very flexible that offers ‘Crowdfunding’ under ‘Regulation CF’. This was an act of Congress almost two decades ago intended to democratize early stage investing – i.e. give average retail investors like you access to early stage companies that previously only venture capital firms or very wealthy ‘Angel’ investors could access. Here’s some more info:
On StartEngine, everyday people can invest and buy shares in startups and early stage companies. There is also a robust ’secondary’ market that offers investors liquidity if desired even before a company has gotten to an ‘exit.’ The minimum is $500 and max is whatever you please.
Everything you need to register and purchase is right on our campaign page:
If there are any other questions or information requests I can address about our company, if you would like you can schedule a 15 minute Zoom meeting with me here:
What is the minimum amount to invest?
On StartEngine, everyday people can invest and buy shares in startups and early stage companies. There is also a robust ’secondary’ market that offers investors liquidity if desired even before a company has gotten to an ‘exit.’ The minimum is $500 and max is whatever you please.
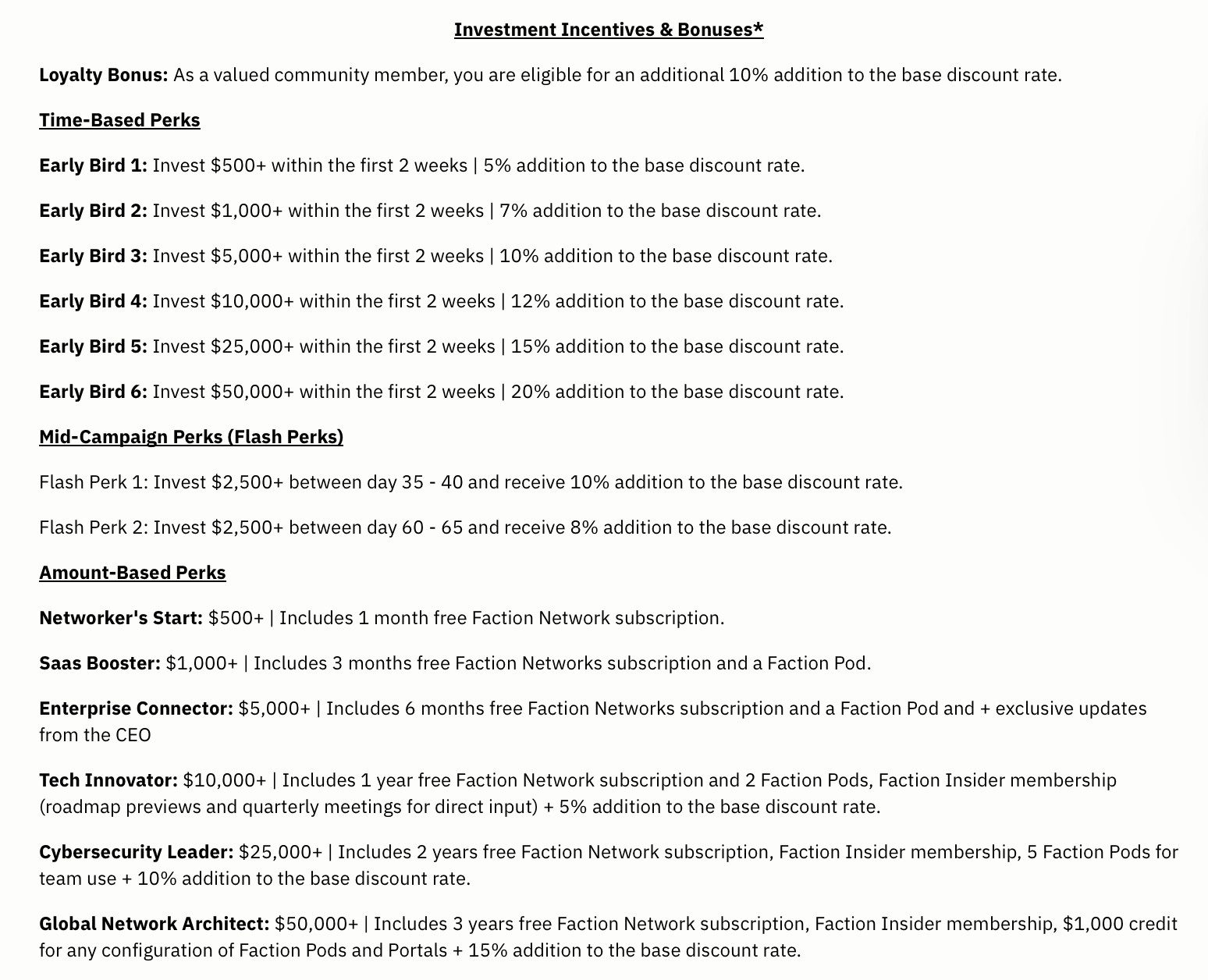
What Are the “Bonuses” on StartEngine?
The StartEngine platform offers a variety of incentives to investors based on either timing or the amount of investment. These work just like the ‘conversion bonus’ of any convertible note. They are in addition to what the default is set.
Here is the set that are offered for Faction Networks. All of the details are on the StartEngine offer page:
I need to know how can I make money?
This a Convertible Note offering. At the time of the first ‘priced round’ – which we expect to be towards the end of the summer – it will covert to equity at either:
- 20% discount to the valuation set in that round; or
- $10M maximum valuation cap.
While there is no guarantee, we are setting a target for $20M valuation or above on our first priced round. We hope that with all of the traction & milestones we can achieve in the interim that we can significantly outperform that target.
Going forward, as the company progresses to our launch and growth, then valuation will increase. Typically, a SaaS product company that is doing well sees between 5x – 7x of what’s called ‘Annual Recurring Revenue’. StartEngine has a ’secondary’ market on the platform for investors wish to get liquidity prior to our company reaching an ‘exit’ through either sale or in best case an IPO.
In the best case of an IPO or mergers / acquisition of the company, then the valuation price versus the valuation you purchased at is the driver. For example, if the company were sold for $1 Billion valuation, that is 100x the valuation cap of this convertible note. Another factor that is unknown currently is ‘dilution’ – if and when the company raises more capital, then more shares are issued. That can affect how proceeds are split up among shareholders, as the per share price is set by the total valuation divided by the number of shares outstanding. On the other side, a company which grows that large and that fast often does ‘stock splits’ and other things which benefit shareholders.
Thus, there is no exact way to predict all these possible scenarios. But in that scenario – typically called a ‘Unicorn’ – the outcomes are generally very good for all investors. These kind of very large multiple returns is the heart of what venture capital is about – and StartEngine is about making that accessible to average investors.
Like any venture capitalist, we would recommend that investors on StartEngine think in terms of a portfolio of investments. Some will do extremely well – and we hope Faction Networks will be one of those. Others will bring a modest return. Some will lose money – which can be up to the entire amount invested. But over a well constructed portfolio, the returns will be very good.
If there are other questions or information you would like, you can schedule a 15 minute Zoom meeting with Geoff Halstead, Faction Networks Co-Founder and CPO here:
.
Escrow Mechanism on Start Engine Campaign
Fund stays in an escrow account until we hit either:
- Minimum of $124K raised; or
- End of the campaign – 3 months.
So, it’s unlikely but if we don’t achieve either of those, then all the funds in escrow are returned to investors.
There is also a notification period after we hit the $124K – and each subsequent milestone when we are allowed to drive – which gives investors the opportunity to change their mind.
How can I learn more about investing on StartEngine
StartEngine is one of the largest, most successful and established crowdfunding platforms, with a very large and growing audience of active investors. You can learn more about them and crowdfunding here.
Pricing Plans
What is the Difference Between Network vs. Private Groups
Network Groups are available by default to all users on the Faction Network. All users can see them and join any Network Group. The owner of the Network Group is notified of each user that joins it. Only Network Owners and Group Managers can create Private Groups.
Private Groups are visible and accessible only to the users that have been invited and authenticated by the Group’s owner. Only Network Owners and Group Managers can create Private Groups. It is important to note that in Faction, Private Groups are truly private!
By default:
- When a Group Manager creates a Private Group, it is encrypted with a private key created and controlled ONLY by the Group Manager.
- Faction Network owners can see the number and size of Private Groups that have been created by a Group Manager but cannot access them and do not know anything about their users.
- Group Managers can invite and authenticate Guest Users directly into a Private Group.
- Guest users will become members of the Faction Network and require a Member license, but do not have access to Network resources, groups, devices or users.
- Network Owners will receive a notification and must approve the request from a Group Manager to add a guest user.
Optional settings are available in the Network Owner Dashboard whereby:
- These powers for Group Manager can be restricted; and/or
- The Network Owner(s) can limit Group Managers to inviting only existing network users which can only be invited and authenticated by and thus are known to the Network Owner.
- The Network Owner(s) can be added to every Private Group by default (which is the only way for the keys to be shared with them).
What Are Personal Devices?
These are the personal devices that are in a licensed user’s profile – i.e. PC, laptops, smartphones, tablets, etc. They are for personal use and all activities and operations within the Faction Network can be applied to that entire users set of devices. User can share folders and files from and between personal devices, but they cannot share access or use of the device itself. That is what Network Devices are for.
What Are Network Devices and Resources?
These are any device or resource which is connected and shared at the Faction Network level. You can think of this like a Cloud Drive. These are devices or resources which you wish to share with all users and devices on your Faction Network.
- Device examples: printers, NAS drives, local data servers, smart manufacturing & infrastructure devices, etc. –
- Resource examples: cloud servers, gateways to legacy LANs, etc. –
What Are Guest Users?
A Faction Network is like a private and secure Internet of your own. Your network and connections are all invisible to anybody outside, and all of the data within it – in transit and at rest in the Cloud and on endpoints – is encrypted with your keys.
By default, every user (Members, Group Managers and Network Owners) and device invited and authenticated onto a Faction Network have access to:
- all users on the Network;
- all Network Groups and Devices; and
- the users and devices within Private Groups to which they are invited and authenticated.
This is generally what is needed for anyone that you are working, collaborating or playing with closely within your organization, workgroup, team, etc.
Guest Users enable you to flexibly address all the other cases that can arise where you need to keep access limited and/or privacy maximized. These are just a few examples.
- Work groups for vendors, service providers, etc.
- Controlling and restricting access to sensitive resources (e.g. Cloud servers, code repositories, etc.) to outside developers, MSPs or IT support.
- In a news organization, enabling a reporter to have completely anonymous and private groups for tips and sources.
- Any situation where you or a team member needs to work collaboratively but closely with teams and devices that should be private and separate from your network and other users.
Who Should I Purchase Member Licenses For?
Member Licenses are for everyone else that just needs to access and use your Faction Network to work, play or otherwise collaborate in a private, secure way. Members can join your network and access all users and devices in groups to which they are invited all base features as listed.
Who Should I Purchase Full Licenses For?
Full licenses are for power users – team member that need to control user access and permissions, and leverage advanced features. Full Licenses also come with the complete suite of all features that are available for each package.
Network Owners
Each customer gets one Faction Network, and Network Owners are the users that have the permission and power to control it and all the users and devices that have access to it. Just think of them as Admins,
Group Managers
Group Managers can create and control private groups that have their own keys. Faction Network owners can see Private Groups
Pods
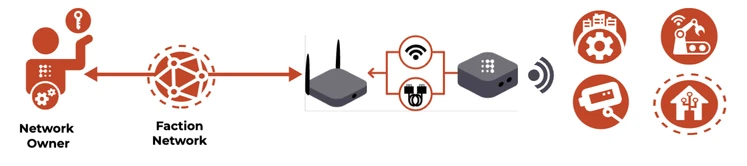
What does a Faction Pod do?
Faction Pods enable you to secure access to ALL the devices and gadgets that have become so critical to our lives for both work and play, extending its protective cloak beyond the usual suspects like PCs, laptops and smartphones.
It does this by simply taking any device that connects to it OFF of the Internet and into your completely invisible and private Faction Network created, controlled and visible only to your organization and users and devices that you have personally authenticated.
I am a WifI Pod / Router OEM. Can we get Faction firmware to make them secure?
Absolutely! Faction will be happy to create custom firmware, or support your routers with extensions in your marketplace. Please contact us for a consultation.
I don’t see a Pod that matches the capabilities I need
If you have custom needs – whether because of a large facility, special types of devices or would like to use existing routers you already have standardized on, talk to us! Any type of router or routing device can be configured to use Faction firmware. We would be happy to work together with you and engage in discussions with the OEM as needed.
My Facility is large and spread out. Won’t It be expensive to deploy Pods?
One of the great things about Faction Pods is their flexibility and low cost. These are totally off-the-shelf devices – we have selected three which have a range of capabilities and corresponding cost – to flex to different use cases. Our lowest cost unit is simply a Wifi extender, so it is easy to deploy lots of them.
Support and maintenance are also simple! If there is a problem with a Pod, you simply replace it, scan and adopt it in seconds and you are back online. No support calls or hours of troubleshooting soaking up your IT staff time!
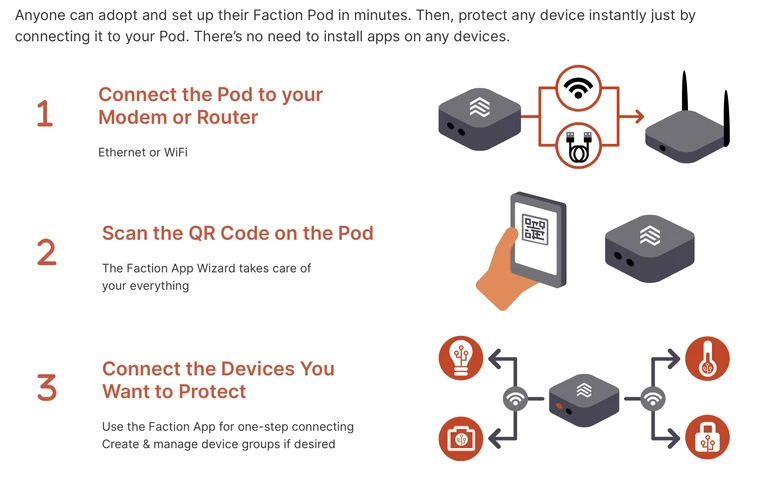
How long does it take to set up and configure Pods?
Anyone can adopt and set up their Faction Pod in minutes. Then, protect any device instantly just by connecting it to your Pod. There’s no need to install apps on any devices.
How do Faction Pods keep these devices secure?
Faction Pods security architecture and core functionality rest on three key principles.
- Complete Decentralization: Keys Are Created and Controlled by YOU. The key you use to adopt a Faction Pod is the Faction Network key created and controlled by you on your endpoint devices. NOBODY – including Faction Communications Corp. – has knowledge or access to this key.
- Direct, Out-of-Band Authentication. Unlike traditional VPNs or SDNs, the Faction Pod employs a unique out-of-band method of invitation, authentication and key exchange that is impervious to external observation or attack of any kind.
- Network Invisibility: Once adopted into your Faction Network, everything that you connect via WiFi behind the Pod is invisible and inaccessible to the Internet – and all the external scanners and probes the permiate it. This effectively eliminates the Internet attack surface by preventing hackers from even identifying your network’s presence.
This unique architecture extends protection beyond traditional endpoints like laptops and smartphones to all the other kinds of smart devices and ‘dumb’ devices that populate our homes and workplaces – and now even our bodies – today.
What About VPN Routers and Firewalls?
Many people that use VPNs also get VPN Routers in an attempt to protect their cameras, gadgets, devices, smart home hubs and otherwise. While VPNs Routers have some utility, they do NOT protect your privacy, security and control of these types of devices. By definition, the types of devices that Faction Pods are designed to protect:
- do not have sufficient resources for encryption and/or programmable UIs (user interfaces); or
- are legacy devices with outdated or sometimes completely discontinued OS which are cannot be supported or upgraded; or
- are IOT devices (sensors, controllers, etc.) which do not even have an OS or even Wifi.
So, either they cannot be connected to the router, or if they are connected via WiFi their security is only as good as the VPN itself.
Firewalls are then often added to try to ‘wall’ off access to certain parts of local networks. But these are trivial to penetrate even without compromising the VPN itself.
What Kinds of Devices Do Faction Pods Secure?
Here’s a breakdown of the kinds of device that Faction Pods can keep safe.
- Smart and Dumb Devices that do not have sufficient resources for encryption and/or programmable UIs (user interfaces), such as:
- Most Web cameras used for home and workplace security;
- printers and Smart Office gadgets of all kinds;
- Smart Home devices like Smart TVs, thermostats, ovens, light bulbs, etc.
- network attached storage devices;
- home and personal medical devices;
- and so on.Printers, NAS drives,
- Smart Manufacturing Devices such as:
- robotics, drones, etc.
- Legacy Devices – whether PCs, servers or embedded in a machine that costs millions of dollars, these are often too expensive and critical to replace, and cannot be upgraded.
- IOT Devices which do not even have Wifi
- Sensors, monitors and controllers of all kinds;
- anything which can plug into a USB or connects back to routers in any way.
By safeguarding both traditional and often-overlooked devices, the Faction Pod creates a holistic security ecosystem for your entire home network. Think of it as a comprehensive security blanket that wraps around all your gadgets, big and small, keeping them safe from the digital wolves at the door.
Remember, the Faction Pod’s invisibility and zero-knowledge encryption work their magic regardless of the device’s technical sophistication. So even those “dumb” devices, once considered easy targets, can now enjoy the same robust protection as their smarter counterparts.
- Smart and Dumb Devices that do not have sufficient resources for encryption and/or programmable UIs (user interfaces), such as:
What is a Faction Pod and What Does It Do??
It is an ordinary, off-the-shelf wireless router that has been transformed into a Faction Pod which features invisibility, advanced encryption and completely decentralized creation and control of keys by YOUR to power comprehensive home device protection. The beauty is its simplicity:
- The Pod can only connect to your Faction Network, and is thus invisible and inaccessible to the Internet.
- But it is still just a WiFi router, so you can connect all your devices to it in the same way and now they are OFF of the Internet but still completely available to you through your Faction Network.
We start with an off-the-shelf router – we have pre-selected, tested and control the inventory of the ones that we offer – and perform two steps:
- flash and install open source routing software;
- configure it with Faction firmware.
The result of these two steps – thanks to the Faction platform – is a breakthrough next-generation wireless router that enables you to control and secure access to all the kinds of devices that VPNs, SDNs and other solutions struggle to protect.
For now, we have selected, tested and carefully control all the steps of configuration for 3 models of WiFi routers to ensure their integrity and security. But the beauty of the Pod is that ANY router or routing device can be installed and configured with the Faction firmware to gain the same capabilities and benefits.
Pilot Program
What do you mean by “IOT Devices”
IOT Devices tend to have lots of different definitions – and of course this is an incredibly broad space. We are talking about any “thing” which lack computing resource beyond its core function, but can plug into a USB or connects back to routers in any way. Generally, this is sensors, monitors and controllers of all kinds – whether they are in factory, office or home settings.
What do you mean by “Legacy Computing Devices”
The world of Smart Manufacturing and eHealthcare are permeated with legacy Devices – whether PCs, servers or embedded in a machine that costs millions of dollars, these are often too expensive and critical to replace, and cannot be upgraded.
Are all of the features available now?
No, this is a pre-commercial release private beta version of Faction VPCs focused on the core functionalities:
- Creating and controlling secure, private Faction Networks;
- Adding and managing users – Network Owners, Group Manager and Member;
- Adopting Pods and adding and managing devices they protect;
- Creating and managing Faction Groups to control access for users and devices;
- Private Email and Faction P-Drop file sharing.
During the course of the pilot, new features will be rolling out as move towards our commercial launch. You will also have the opportunity to bring your voice to our priorities and even new features as we learn and understand your needs.
Why do you call this a “Virtual Private Circuit”?
There was a day when no organization would have ever considered connecting mission critical devices – such as smart manufacturing machinery, home and personal healthcare devices, charging stations and other decentralized infrastructure – directly to the Internet. It is simply too risky.
For 30 years, organizations leased T-1 lines, a secure but costly way to have a totally private network to connect critical machines and devices and the computers and servers that are needed to monitor and control them. But then, something happened: T-1 lines were phased out! One by one, these internal networks were moved onto the Internet and securing these connections become the job of VPNs, Firewalls and SDNs.
Unfortunately, the Internet is fundamentally compromised and more organizations are discovering every day that these tools simply cannot secure mission critical machines and devices/ That’s Why We Created the Faction Virtual Private Circuit
It’s a Simple but Powerful Idea: get your critical users, devices and systems – including cloud servers – OFF of the Internet and into your secure, private Faction Virtual Private Circuit. So, it is similar to the old T1s, but more secure, far less expensive, far more flexible and far easier to manage – or all the expensive hardware and software that is thrown at the unsolvable problem of keeping devices which are connected to the Internet safe!
What is a Virtual Private Circuit?
The Faction Virtual Private Circuit (VPC) is a Business VPN replacement for small to midsized organizations or collaborative teams that need to secure distributed workplaces with lots of smart, dumb and legacy devices. VPCs:
- Eliminate the vulnerabilities of VPNs;
- Avoid the pain, complexity and costs of SDNs/ZTNA;
- Help protect your organization – and customers / users – from catastrophic attack.
How Will Participating Benefit Me?
By becoming one of our early adopter pilot customers and partners, your organization will realize multiple benefits:
- long term licensing discounts;
- free custom deployments and support – and where applicable and feasible – integrations; and
- a voice in our roadmap priorities.
Of course, while gaining all of this, you will be take a major step forward to help protect your workplace, distributed workforce and factories from catastrophic attacks.
What is the Faction Pilot Program and Who Should Apply?
The Pilot Program enables organizations in our focus verticals for launch:
- Manufacturing;
- Healthcare;
- Green Energy
to gain early access and full deployment of Faction Networks and Pods at absolutely no cost. We are focused on:
- small to mid-sized businesses;
- MSPs and other IT and cybersecurity service providers that have customers in these verticals.
We also are doing a number of pilot deployments in partnership with larger organizations in each of these verticals. We are certainly open to exploring all such opportunities, but will want to be sure we can properly execute and support all pilots. So please do contact us for a consultation.
What Will I do with Faction Pods If I Don’t Continue?
If you do not continue on to a commercial license with us, you can simply return all of the Pods.
What Kinds of Cameras Can be Secured by Faction Pods
Any type of Web-enabled camera which is external to a PC, Laptop, Smartphone, etc. and will connect via either WiFi or Ethernet to a router in order to transport its video data feed. If it can be connected to a router, it can be connected to a Pod in exactly the same way.
ASA Premium Service
Why is there a minimum fee for a Threat and Vulnerability Assessment?
We use various security tools to provide actionable information to our clients. Due to the highly sensitive nature of the reporting outputs, we use payment as part of the identification, verification, and screening process to prevent abuse. You must be the owner or operator of the system or have explicit authorization for us to conduct a vulnerability security assessment on behalf of your organization.
Conducting a vulnerability assessment takes time and resources to address in a professional and thorough manner while providing rapid response. Please fill out our registration form to schedule a consultation to determine if your organization qualifies for any special programs.
Can I get an assessment against client systems?
Of course! Agencies and consultants can use this service to perform security reviews of sites they are handing over or working on. A value added service for your web projects or managed services.
Who uses these Services?
Organizations of all sizes in many industries are concerned with understanding and mitigating vulnerabilities to internet-based attacks. Not all organizations face the same threats, and the nature and targets of threats are constantly changing. Our services are designed to address the needs of many industry verticals.
Our Industry Exposure Reports are for organizations that want to get a current picture of the exposed hosts using applications and services in their industry vertical, and where they should focus their attention to formulate defences. This report is available to any organization worldwide.
Our Threat and Vulnerability Assessment services are popular with anyone who wants to understand the exposure and vulnerabilities in the security postureof their specific organization with regard to internet exposed networks, devices and data. Currently, these services are restricted to organizations in North America[GM1] , which can vary from small business to large enterprises.
Our Threat Analysis and Reconnaissance services are for organizations that have reason to believe that they may be under current or imminent attack. Typically, this is due to a specific cause for concern, such as:
- Warnings or alerts from the media, cybersecurity and/or law enforcement agencies relevant to your industry vertical or organization;
- Poor network performance or unusual behavior from IT equipment and concerning computer activity observed by staff;
- Amplified alerts from virus monitoring tools, increased volume of phishing emails, and application or computer lockups;
- Concerns of active threats resulting from an initial Industry Exposure Report;
- Discovery of specific vulnerabilities resulting from a Threat and Vulnerability Assessment.
[GM1]Why is this restricted to organizations in North America?
What are the typical targets of the assessment service?
The assessment locates connected devices that host network services and run various applications accessible from the internet, such as:
- Web hosts, including private web servers
- Virtual hosts, such as virtual servers (both IP-based and name-based)
- Cloud storage servers
- Private VPN’s
- Firewalls
- Wireless Access Points
- Internet connected devices, such as web security cameras, sensors, healthcare devices, manufacturing equipment, and other smart and dumb devices.
You can specify individual IP addresses, network ranges, and include your domains for the assessment. However, for large and highly distributed deployments such as remote sensor or industrial processing networks, you should contact us to discuss customized options.
Can our integrations with 3rd party vendor equipment be included?
Yes, if you have systems installed or integrated with 3rd party vendors, let us know and we can include them in our scans and analysis.
What does the Threat and Vulnerability Assessment Include?
- We provide an inventory report of exposed host IP addresses, open services on those hosts, assets at a particularly high risk of adversary exploitation, and potential vulnerabilities of those hosts in the context of an organization’s network security posture.
- Recommendations on steps for mitigation or remediation, if further investigation is warranted, and key focal points.
Will Faction partner with other organizations for attack surface assessments and threat analysis?
Certainly! However, this area has many different tools, consultants and contractors, which makes it very challenging and complex for the average small to mid-sized business user to sort out the wheat from the chaff.
Or in some cases, it can be far worse. When it comes to VPNs – and cybersecurity tools – there are actually very large numbers of apps which are malware created by both criminal gangs and hostile state actors.
Therefore, Faction will go through a careful vetting process of any organizations that we recommend and/or partner with, and certainly expects the same in return! There is nothing more important to us then the security and privacy of our customers and users.
What % of these fees does Faction Communications get?
The Mobile Intelligence Alliance, a non-profit 503(c)3 corporation, provides all of the professional services and analysis and keeps 75% of the fees. Faction Communication Corp. keeps 25% of the fees to cover the following:
- e-commerce and other processing costs;
- scheduling and management of customer engagements;
- proprietary tools, databases and expertise that we provide in delivery of these services.
Our partnership with Mobile Intelligence Alliance is based on our shared goal to help average users and small to mid-sized businesses to increase their understanding and awareness of the many threats to their security and privacy, and enable them to do something about it.
Faction Communications is open to and engaged in discussion with other partners in this area. Professional services is not a long term component of our business model, which is focused on our SaaS platform, applications and solutions.
What does the Threat Analysis and Reconnaissance package include?
- Report. We compile a report after conducting an analysis of the results from the active and passive security tools. Sections include an overall summary of the results, including vulnerabilities found, a list of discovered vulnerabilities with recommended remediation steps, and an inventory of exposed assets in an appendix that contains the raw results and screenshots from the tools that used during the assessment.
- Presentation & Consultation. We conclude with a 1 hour working consultation to walk through the results, answer any questions, and ensure that you have actionable findings.
- Next Steps and Follow Ups. If necessary, we can schedule additional periodic analysis and reconnaissance of your network or refer you to managed security or forensic professionals based on the results. (These are optional and would depend on your choice of follow-on actions and expertise required to address any identified attacks or compromise).