Source code inspected by independent cyber labs
Faction Pods & Portals
Finally, Protect Your Cameras, Gadgets and Networked Devices in Your Smart Home and Office - and Smart Manufacturing and Infrastructure

Our Breakthrough Gateway for Your Faction Network



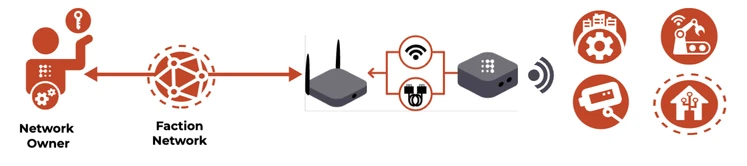
All of the devices you connect to your Pod are invisible and inaccessible to the Internet, but completely visible and controlled by YOU in your Faction Network
Zero Trust Secure Networking & Smart Hardware
A Pod or Portal for Every Use Case
SOHO

Pod



Securing remote teams and devices in Small Office / Home Office environments
Business
Business Portal

Factories & Business Locations can put everything on a Faction Network with no changes
HaLow

HaLow Portal

HaLow Routers with up to 9 mile range address industrial, agriculture, smart infrastructure, etc.
5G Puck

For smart city / infrastructure use cases
All of the devices you connect to your Pod are invisible and inaccessible to the Internet, but completely visible and controlled by YOU in your Faction Network
Faction Pods are Easy, Fast, Low Cost and Flexible to All of Your Needs and Use Cases
Keep Your Cameras Private
Secure Your Printers and NAS Drives
Secure Your Networked Dumb Devices
Build Your Own Pod Network
Keep Your CCTV Cameras private
Protect Your Manufacturing & IOT Devices
Secure Smart Infrastructure
Secure Access to Cloud Servers and Data
Protect ALL of Your Devices and Gadgets
VPNs only protect computing devices - things like PCs, Laptops, Tablets and Smart Phones. Faction Pods enable you to protect the privacy and security of ALL the devices and gadgets that have been so critical to our lives for both work and play.
Devices that do not have sufficient resources for encryption
Devices that do not have programmable UIs (user interfaces)
Legacy computers and smart machines that cannot be upgraded
A REALITY CHECK FOR VPN ROUTERS
Many people that use VPNs also get VPN Routers in an attempt to protect their cameras, gadgets, devices, smart home hubs and otherwise. While VPN Routers have some utility, they do NOT protect your privacy, security and control of these types of devices.
Learn WhySet Up in Minutes
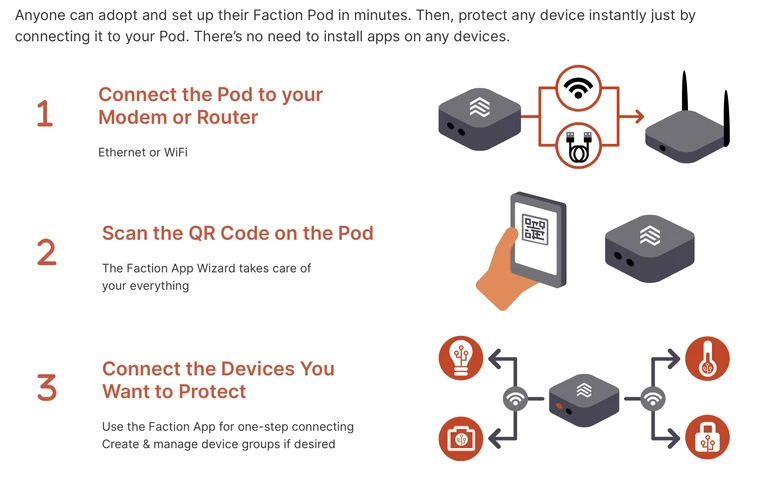
Anyone can adopt and set up their Faction Pod in minutes. Then, protect any device instantly just by connecting it to your Pod. There’s no need to install apps on any devices.
Connect the Pod to your Modem or Router
Ethernet or WiFi
Scan the QR Code on the Pod
The Faction App Wizard takes care of your everything
Connect the Devices You Want to Protect
Use the Faction App for one-step connecting
Create & manage device groups if desired
Cameras
Do you know who is looking at your camera feeds? REALLY? Think again!
Faction Pods ensure that only YOU control access to cameras and their data streams.Smart Manufacturing
The modern factory floor is a complex mix of legacy and new machines - and since the demise of the T1 line, most are connected to the Internet.
Smart Infrastructure
All manner of sensors, smart gadgets and robots watch over and serve us these days.
Networked Appliances
Our printers, stoves - even furnaces and thermostats - are now all connected and exposed to malicious actors.
Networked Data Storage
Network Attached Storage (NAS) device, external drives and other types 'dumb' storage devices all depend on the protection of Firewalls and other security on your local network.
Smart Home Hubs
These evade your VPN firewalls and other protections to send your data back and forth directly to their cloud servers. The devices still can't encrypt their data traffic, and are still on IP, so can be attacked directly through your router.
Frequently asked questions
What is a Faction Pod and What Does It Do??
It is an ordinary, off-the-shelf wireless router that has been transformed into a Faction Pod which features invisibility, advanced encryption and completely decentralized creation and control of keys by YOUR to power comprehensive home device protection. The beauty is its simplicity:
- The Pod can only connect to your Faction Network, and is thus invisible and inaccessible to the Internet.
- But it is still just a WiFi router, so you can connect all your devices to it in the same way and now they are OFF of the Internet but still completely available to you through your Faction Network.
We start with an off-the-shelf router – we have pre-selected, tested and control the inventory of the ones that we offer – and perform two steps:
- flash and install open source routing software;
- configure it with Faction firmware.
The result of these two steps – thanks to the Faction platform – is a breakthrough next-generation wireless router that enables you to control and secure access to all the kinds of devices that VPNs, SDNs and other solutions struggle to protect.
For now, we have selected, tested and carefully control all the steps of configuration for 3 models of WiFi routers to ensure their integrity and security. But the beauty of the Pod is that ANY router or routing device can be installed and configured with the Faction firmware to gain the same capabilities and benefits.
What Kinds of Devices Do Faction Pods Secure?
Here’s a breakdown of the kinds of device that Faction Pods can keep safe.
- Smart and Dumb Devices that do not have sufficient resources for encryption and/or programmable UIs (user interfaces), such as:
- Most Web cameras used for home and workplace security;
- printers and Smart Office gadgets of all kinds;
- Smart Home devices like Smart TVs, thermostats, ovens, light bulbs, etc.
- network attached storage devices;
- home and personal medical devices;
- and so on.Printers, NAS drives,
- Smart Manufacturing Devices such as:
- robotics, drones, etc.
- Legacy Devices – whether PCs, servers or embedded in a machine that costs millions of dollars, these are often too expensive and critical to replace, and cannot be upgraded.
- IOT Devices which do not even have Wifi
- Sensors, monitors and controllers of all kinds;
- anything which can plug into a USB or connects back to routers in any way.
By safeguarding both traditional and often-overlooked devices, the Faction Pod creates a holistic security ecosystem for your entire home network. Think of it as a comprehensive security blanket that wraps around all your gadgets, big and small, keeping them safe from the digital wolves at the door.
Remember, the Faction Pod’s invisibility and zero-knowledge encryption work their magic regardless of the device’s technical sophistication. So even those “dumb” devices, once considered easy targets, can now enjoy the same robust protection as their smarter counterparts.
- Smart and Dumb Devices that do not have sufficient resources for encryption and/or programmable UIs (user interfaces), such as:
What About VPN Routers and Firewalls?
Many people that use VPNs also get VPN Routers in an attempt to protect their cameras, gadgets, devices, smart home hubs and otherwise. While VPNs Routers have some utility, they do NOT protect your privacy, security and control of these types of devices. By definition, the types of devices that Faction Pods are designed to protect:
- do not have sufficient resources for encryption and/or programmable UIs (user interfaces); or
- are legacy devices with outdated or sometimes completely discontinued OS which are cannot be supported or upgraded; or
- are IOT devices (sensors, controllers, etc.) which do not even have an OS or even Wifi.
So, either they cannot be connected to the router, or if they are connected via WiFi their security is only as good as the VPN itself.
Firewalls are then often added to try to ‘wall’ off access to certain parts of local networks. But these are trivial to penetrate even without compromising the VPN itself.
How do Faction Pods keep these devices secure?
Faction Pods security architecture and core functionality rest on three key principles.
- Complete Decentralization: Keys Are Created and Controlled by YOU. The key you use to adopt a Faction Pod is the Faction Network key created and controlled by you on your endpoint devices. NOBODY – including Faction Communications Corp. – has knowledge or access to this key.
- Direct, Out-of-Band Authentication. Unlike traditional VPNs or SDNs, the Faction Pod employs a unique out-of-band method of invitation, authentication and key exchange that is impervious to external observation or attack of any kind.
- Network Invisibility: Once adopted into your Faction Network, everything that you connect via WiFi behind the Pod is invisible and inaccessible to the Internet – and all the external scanners and probes the permiate it. This effectively eliminates the Internet attack surface by preventing hackers from even identifying your network’s presence.
This unique architecture extends protection beyond traditional endpoints like laptops and smartphones to all the other kinds of smart devices and ‘dumb’ devices that populate our homes and workplaces – and now even our bodies – today.
How long does it take to set up and configure Pods?
Anyone can adopt and set up their Faction Pod in minutes. Then, protect any device instantly just by connecting it to your Pod. There’s no need to install apps on any devices.
My Facility is large and spread out. Won’t It be expensive to deploy Pods?
One of the great things about Faction Pods is their flexibility and low cost. These are totally off-the-shelf devices – we have selected three which have a range of capabilities and corresponding cost – to flex to different use cases. Our lowest cost unit is simply a Wifi extender, so it is easy to deploy lots of them.
Support and maintenance are also simple! If there is a problem with a Pod, you simply replace it, scan and adopt it in seconds and you are back online. No support calls or hours of troubleshooting soaking up your IT staff time!
I don’t see a Pod that matches the capabilities I need
If you have custom needs – whether because of a large facility, special types of devices or would like to use existing routers you already have standardized on, talk to us! Any type of router or routing device can be configured to use Faction firmware. We would be happy to work together with you and engage in discussions with the OEM as needed.
What does a Faction Pod do?
Faction Pods enable you to secure access to ALL the devices and gadgets that have become so critical to our lives for both work and play, extending its protective cloak beyond the usual suspects like PCs, laptops and smartphones.
It does this by simply taking any device that connects to it OFF of the Internet and into your completely invisible and private Faction Network created, controlled and visible only to your organization and users and devices that you have personally authenticated.
Build You Own Pod Networks
Effortlessly build a totally private and secure network to protect and share devices across any number of locations - whether in a large home, office or other property, or multiple sites located anywhere in the world.
Protect Cameras & Devices Spread Across a Large Property
Share and Protect Devices with family, friends & teams across the world
Access Your Home/Office Devices, Web and Streaming While Traveling

Contact Faction
If you would like to join as a partner, invest or otherwise help Faction, get in touch.
Contact Us