It’s not that they are bad. They just do not address the actual root causes of the vulnerabilities to your privacy and security.
Over 1 billion people use VPNs to attempt to protect their Web browsing, networking and data. But what most of these people don’t know is that VPNs share the same 3 core vulnerabilities of all Web infrastructure, which make your privacy impossible to guarantee.
Why VPNs Are Not Actually Private or Secure #
While your VPN tunnel is secure, everything else is vulnerable and can be compromised.
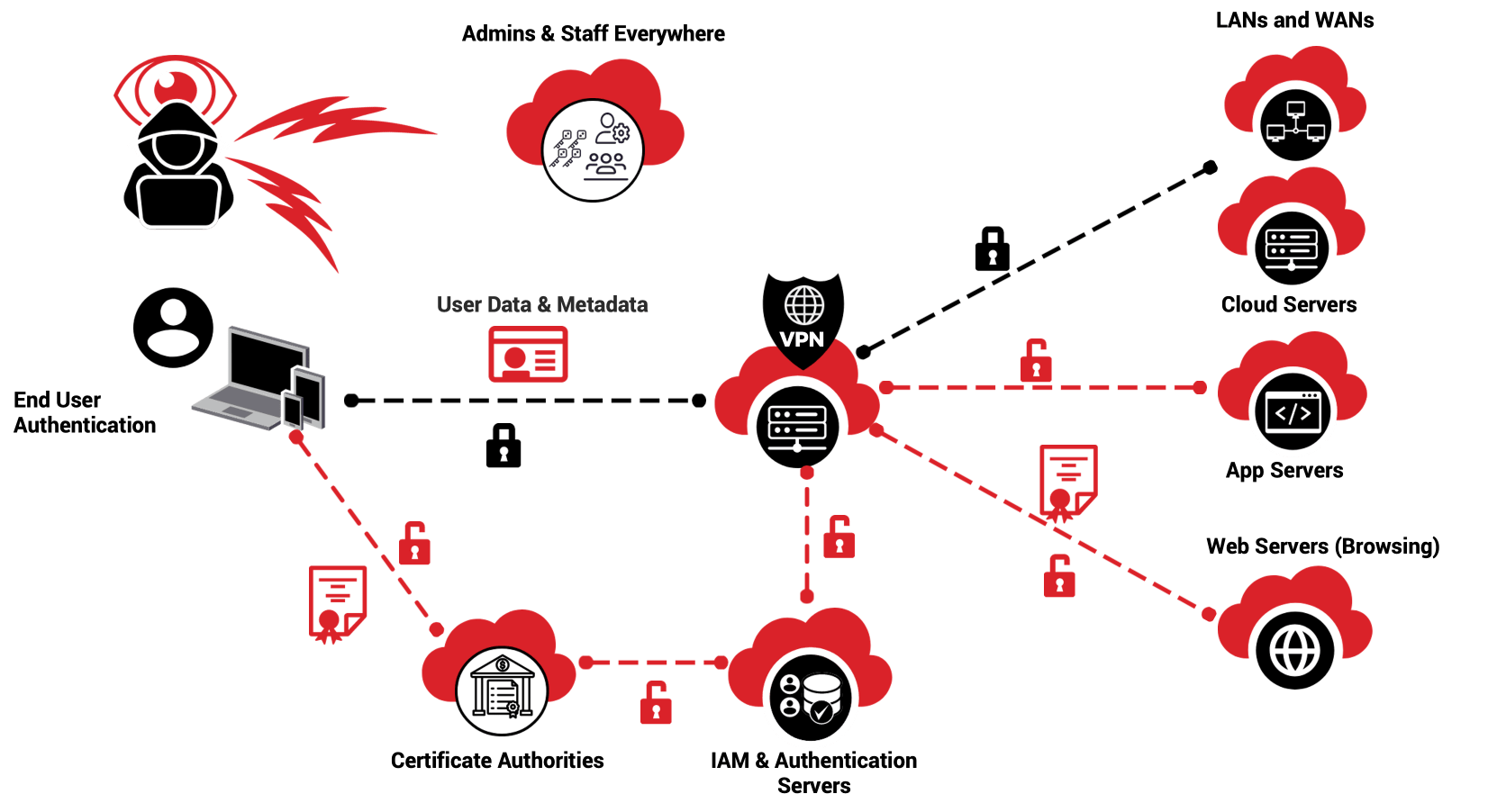
Admins & Staff Everywhere #
Your security is only as good as the lowest paid engineer or disgruntled insider – especially at your VPN company!
Certificate Authorities #
Certificate Authorities are like banks – but far easier to compromise!
The security of all of your other connections and networking on the Web depend on SSL Certificates. These are centralized and run by admins and staff – who can always be compromised. Or no need to bother since Certificates are widely available for purchase on the Dark Web!
IAM & Authentication Servers #
Centralized with Cloud Vulnerabilities
These build a whole new centralized database of user identity and credentials, while still being just as vulnerable to cloud hacks of the servers, admins and staff that control them.
They also depend on user credentials – which are notoriously insecure – and 2FA – which is trivially easy to spoof.
LANs and WANs #
Breaches Are Catastrophic
Your VPN tunnel may remain encrypted, but once the weak points in a VPN are compromised, the attacker can go anywhere in the VPN and the internal local and wide area networks it connects to.
Web Apps #
Out of Scope
When you use and connect to 3rd party Web applications, then you are beyond the scope of VPNs or SDNs and must rely up on their authentication and Web server defenses to protect your connection and your data.
Web Servers #
Are Simply NOT Private at All
Everything you do on the Web is visible and tracked anyways unless you use a Privacy Browser. And even then, there are all kinds of gotchas.
Centralized Architecture & Control #
- Centralized Servers
- Centralized Certificate Authorities
The servers, certificates and people can all be compromised.
Or no need to bother since certificates can be purchased on the Dark Web!
Networks & Connections are Visible and Vulnerable #
Because They Rely Upon Internet Protocol
- With Internet Protocol, network addresses and traffic are visible, and connections are insecure by default
- So the Bad Guys always have the advantage
Data is Vulnerable #
Because it is either not encrypted or someone else has the keys.
There is always someone other than you who has access and control.
End Users are careless and endpoint encryption a poor UX so it is rarely used.
Smart Manufacturing & Infrastructure #
Depend on Firewalls or Nothing at All.
A combination of legacy devices and new very smart machines now populate most floors in the modern manufacturing workplace. Old ones simply cannot be protected – but are too disruptive to replace. New ones may be smart, but rely on precise millisecond-level calibration to which encryption is an unwelcome variable.
Organizations used to rely upon dedicated T1 ‘Circuits’ to keep these isolated, but over the last decade those have been phased out and now most are simply connected – and exposed – to the Internet.
Network Appliances #
Depend on Firewalls.
They just rely on the protection of the gateway into the local network. Some appliances like Network Attached Storage devices and printer / fax / scanners are ‘smart’ enough, but do not have rigorous security or programmable UIs to add encrypted networking.
Smart Home Office Devices #
Cannot Be Protected by VPNs.
These devices do not have sufficient resources or programmable interfaces to support encryption and secure connections, so they are completely exposed to Internet attacks.
Smart Home Hubs #
Evade VPNs and Firewalls.
These evade your VPN firewalls and other protections to send your data back and forth directly to their cloud servers.
The devices still can’t encrypt their data traffic, and are still on IP, so can be attacked directly through your router.