Welcome! #
This article will help to get oriented and moving forward with using and testing Faction Networks and Pods in your pilot. At Faction, we are dedicated to building platforms, apps and tools that enable every day users, small organizations and groups to achieve security and privacy for their networking, communications and data and are:
- Private and Secure;
- Easy to Use; and
- Always, always controlled by YOU
So, our most important criteria for success for our pilot with you will be measured against these goals.
Getting Started #
Get Oriented #
Faction Virtual Private Circuits provide a unique solution to protect critical but vulnerable smart, dumb and legacy devices that populate our lives, workplaces, homes – and even our bodies. The basic idea is very simple:
- Get your critical users, devices and systems – including cloud servers – OFF of the Internet and into your secure, private Faction Virtual Private Circuit which has zero visibility, access or exposure to Internet attacks.
If you already understand all of this, proceed directly to get your app and Pods. If not, we recommend that you read the following articles:
- Introduction to Faction Virtual Private Circuits
How to Get the App #
If you understand what a Faction Virtual Private Circuit is, why you want one, and what you will protect with it, then the next step is to get the app. We are currently in private distribution only, so you do this directly from us or through a private distribution & testing application called TestFlight.
Links #
IoS (iPhone & iPad) – distributed on TestFlight
MacOs:
https://faction.net/downloads/macOs_v_0_9_faction.dmg
Windows:
https://faction.net/downloads/v0_9_faction_windows.zip
Linux:
Coming soon!
How to Get Your Pods #
To get your Pods, just:
- Go to our ordering page;
- Select the number and type of Pods you want; and
- Fill out the shipping information; and
- Purchase them.
We will prepare and ship them to you within several days. If you do not continue on with your Faction Virtual Private Circuit after the pilot is done, you can return your pods. We will send you a return & shipping package and refund your purchase price in full upon receipt of the equipment.
How to Choose Your Pods #
We have 3 different levels of Pods currently, for the 3 most common use cases.
GL.iNet GL-AR300M16 #
This a very low cost and versatile travel router. It’s great for:
- small personal office and travel use cases;
- devices that are spread around a larger facility like cameras, equipment, sensors, etc.
If you are going to attach lots of devices, or devices which need to stream lots of data, you will probably want something more capable.
GL.iNet GL-SF1200 #
This is more capable. It’s great for:
- most small business offices;
- apartments and small homes;
where it has the range and resources to connect all of your smart and dumb devices.
GL.iNet GL-A1300 #
It’s very similar to the SF1200, but has a more powerful CPU optimized for network stability and is designed for users with heavy demand on using VPN networks.
If you have any questions, please contact us and we’ll be happy to help you select your Pods.
Using the App #
The app is designed to be so easy and simple that anyone can use it without any help or support. Of course, that is a goal, and your testing during the pilot will undoubtedly reveal opportunities for improvement!
Starter Videos #
Here are a few quick videos to help you start.
- Creating a Faction Network
- Joining Other Faction Networks
- Joining a Faction Network – prior to creating one.
- Creating Groups and Adding Members
- Managing and Using Private Email
- Adopting a Pod
- Adding Pods to Groups
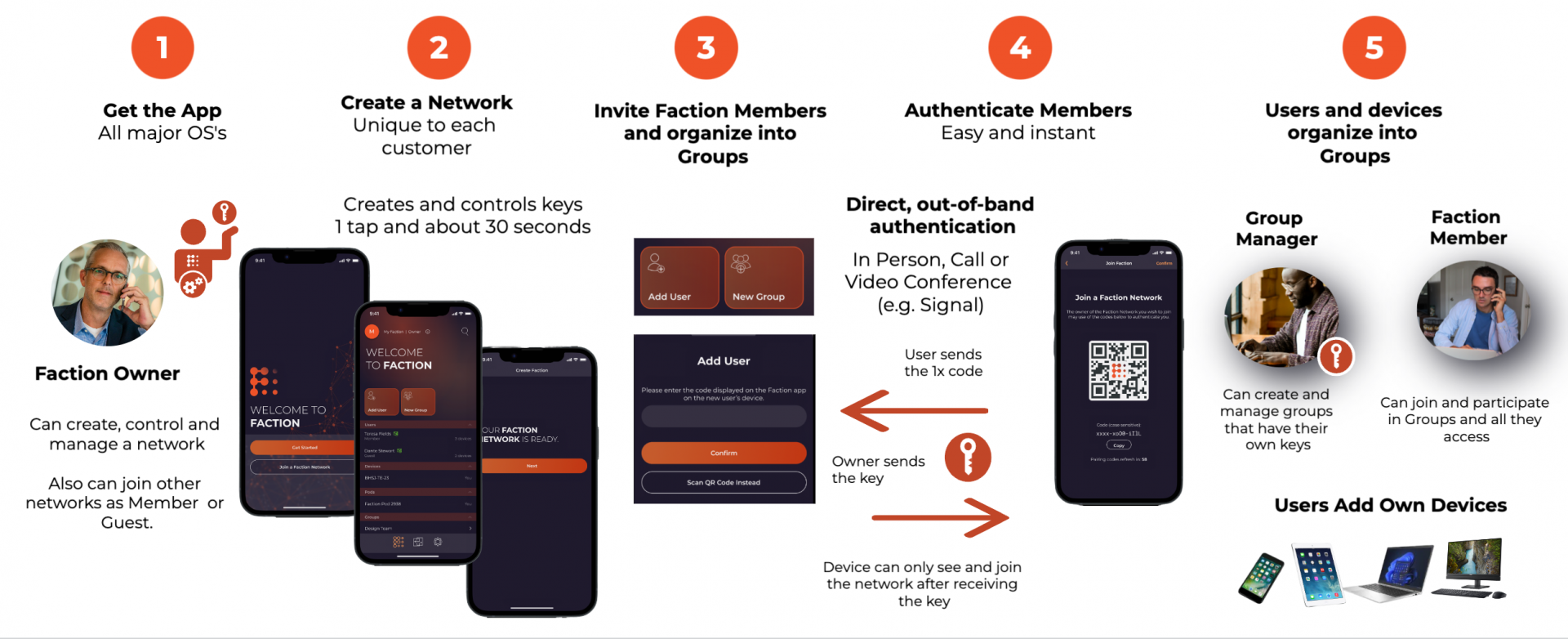
About Faction Out-of-Band Authentication #
When we say “Zero Trust”, we truly mean Zero Trust. Faction does not trust the Cloud – period. Web servers – including Certificate Authorities – can and are routinely compromised by criminal cyber gangs and nation-state hackers.
Therefore, we use a direct, ‘out-of-band’ method of invitation and personal authentication by the Network Owner of users that are added to their Faction Networks. There are no credentials. Only devices and encryption keys. You either have the key – which was given to you by the Faction Network owner – or you don’t. If you have the key, you can see and access the network. If you don’t you can’t.
You will notice when you first invite and add users to your Network (or in reverse join one), that users cannot “request” to join. Rather, the Network Owner invites you by scanning a QR code on your device (or a one-time code can also be input). The process is direct, real time, between the two of you. There is no phishing, spoofing, stuffing or any of the other tricks possible.
What About SSO & IAM support? #
We understand that users value convenience. So, in the future, we will offer support for major SSO and IAM (Identity and Access Management Platforms). But we will first warn you that if your Faction VPC is truly protecting anything that is critical to you or your organization, this is bad idea! Do not trust anything in the Cloud to connect to your VPC. Keeping it private and the keys in control of just a few trusted users is paramount to true security.
About Groups #
Groups are how your organize and manage who has access to what. They work just like Groups you have used in many other SaaS apps – except that with Faction Networks you can add both Users and Devices to them.
There are two levels of Groups
Network Groups #
- Are created by the Network Owner (or Administrators that have been empowered by the Owner).
- Are visible and accessible by default to every user invited and authenticated into the network.
- So, that’s where you should put users, devices – and soon data folders – that you want everyone to have access to.
Private Groups #
- Are created by Group Managers (and the Network Owner can also create Private Groups)
- Are visible and accessible ONLY to the users that are invited and authenticated by the Group Manager.
- In fact, not even the Network Owner has the key to Private Groups which are created by Group Manager. The Network Owner can see them – and controls the permissions of the Group Manager – but does not have the keys.
- So, Private Groups are for uses, devices – and soon data folders – that should be private and shared only within that group.
About User Roles and Permissions #
These are the levels of user roles and powers available currently.
Network Owners #
Each customer gets one Faction Network, and Network Owners are the users that have the permission and power to control it and all the users and devices that have access to it. Just think of them like administrators.
There is one registered customer and master Network Owner. That Network Owner than can share that power with other users.
Group Managers #
Group Managers can create and control private groups that have their own keys. Faction Network owners can see Private Groups, but do not have the keys to access them. Soon, we will make this a configurable setting the the Network Owner decides.
Members #
The Member role is for everyone else that just needs to access and use your Faction Network to work, play or otherwise collaborate in a private, secure way. Members can join your network and access all users and devices in groups to which they are invited all base features as listed on our pricing page.
In the future, we will add a Guest role.
Using Private Email #
Faction data encryption is like PGP on steroids!
You can use your favorite email application, but encrypt the contents of your messages with your own key.You can use Faction for privacy with any native email application that uses X.509 certificates. These are just a few examples.
Using it With Gmail #
You can use Gmail – or any Web mail server – with your device-native applications and will have the same protection.

If you are not familiar with this, here are some support articles.
- How to use Gmail with Outlook
- How to use Gmail with Apple Mail
- How to use Gmail with Thunderbird
Web extensions for Gmail and other Webmail applications are coming soon.
Using Pods #
The idea of a Pod is very simple:
- Faction Pods Take Vulnerable Devices OFF of the Internet and into a private Faction Network that only you – and users and devices that you personally invite and authentic – can see or access.
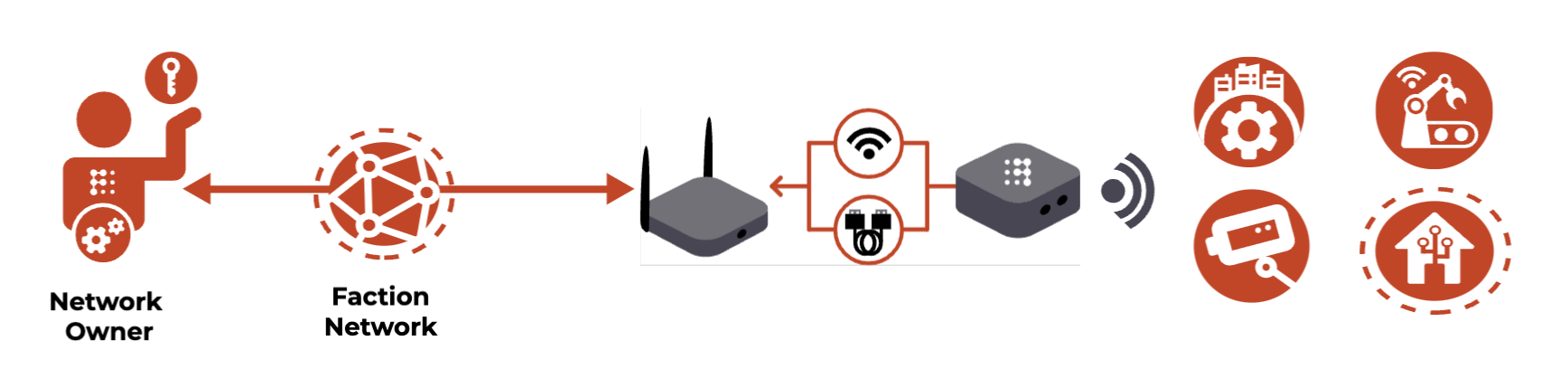
The Pod is a node and gateway for your Faction Network to devices in its physical location. You can connect devices to it via either Wi-Fi or Ethernet. In the future, we will offer more Pods with more options for connecting.
Adopting Pods #
We call the process of connecting and configuring a Pod as a node and gateway on your Faction Network “Adoption”. Anyone can adopt and set up their Faction Pod in minutes. Then, protect any device instantly just by connecting it to your Pod. There’s no need to install apps on any devices.
1. Connect the Pod to your Modem or Router #
You can use either Ethernet or WiFi.
2. Scan the QR Code on the Pod #
The Faction App Wizard takes care of your everything
3. Connect the Devices You Want to Protect #
Currently, you will do this manually following the steps for connecting a WiFi router to any device. We have provided some help tips for that here:
- Connecting devices to your Pods
In the future, the Faction App will help you with connecting devices, as well as labeling and generally managing all devices that Pods connect to.