Weak Protocols and Built-in Back Doors Make These Inviting Targets
The Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Energy have issued multiple alerts for threat actors gaining access to a variety of internet-connected uninterruptible power supply (UPS) devices, often through unchanged default usernames and passwords.
UPS devices provide clean and emergency power in a variety of applications when normal input power sources are lost. Loads for UPSs can range from small (e.g., a few servers) to large (e.g., a building) to massive (e.g., a data center). In recent years, UPS vendors have added an Internet of Things capability, and UPSs are routinely attached to networks for power monitoring, routine maintenance, and/or convenience.
Unfortunately, most UPSs are still monitored using insecure protocols – such as SNMPv1 or v2 – which are known to be highly vulnerable to cyber criminals. Even SNMPv3 includes inherent cyber flaws that make it vulnerable to attack. In addition, many SNMP cards manufactured in China have backdoors that can compromise the UPSs.)
Cybersecurity and Infrastructure Security Agency (CISA)
Recommended Steps
CISA advises the following critical steps to reduce the likelihood of UPS systems being hacked.
1. Ensure UPSs are not accessible via the Internet
Organizations can mitigate attacks on UPS devices by removing management interfaces from the Internet. If remote connection is required – as is usually the case – connecting management interfaces to the Internet is required, secure networking technology to prevent visibility and attack is critical.
2. Change the UPS’s default credentials and Use Strong Passwords
Check to make sure that the username and password are not set to the factory default ― and if they are, update them immediately to strong, long passwords or passphrases in accordance with National Institute of Standards and Technology (NIST) guidelines.
3. Update UPS firmware
In addition to default credentials, threat actors can also use critical security vulnerabilities to enable remote takeovers of UPS devices. Failing to install firmware updates can increase a UPS’s vulnerability to hackers. In fact, Gartner predicts that 70% of organizations that do not have a firmware upgrade plan in place will be breached due to a firmware vulnerability.
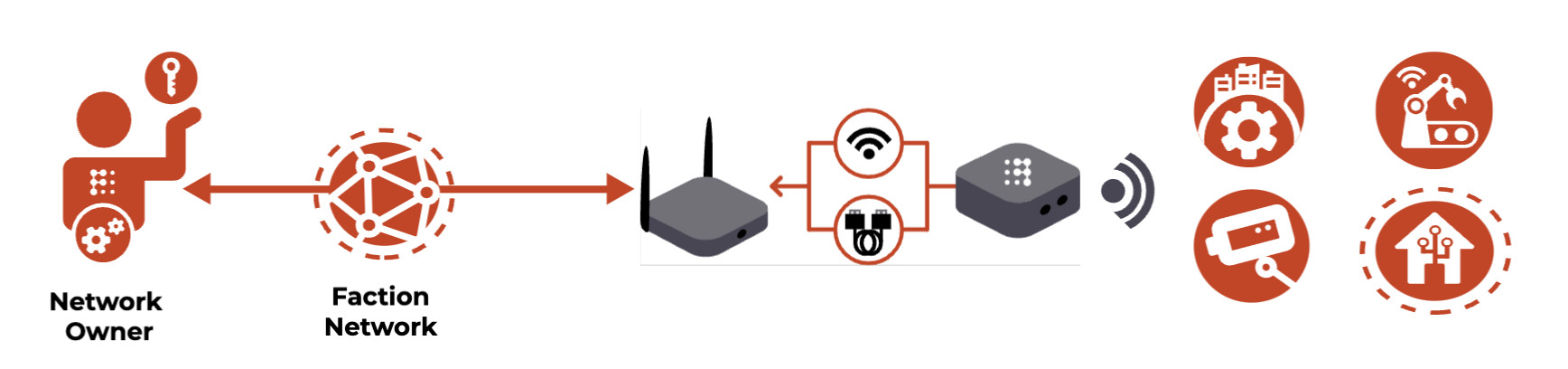
Securing UPS’s with Faction VPCs
A Faction Pod and Virtual Private Circuit:
- makes a UPS invisible and inaccessible to the Internet;
- eliminates passwords and credentials of any kind;
- closes off access to the Internet in both direction – thereby mitigating most backdoor threats.