For most small to mid-sized business owners, just keeping business and operations running is the primary concern. When one looks at all of the potential threats, and all of the steps that are required to implement a complete and rigorous cybersecurity defense, it can be very hard to know where to start.
Here is a simple guideline for the 5 easy first steps you can take to reduce the most critical vulnerabilities that are most likely to directly threaten your business production line and operations.
1. Know Your Attack Surface: See What an Attacker Can See
You have probably done a lot to secure your facilities. However, without visibility into your assets that are
accessible across the Internet, you may not fully understand your potential for being attacked. While many people use search engines to find cat pictures, cyber attackers commonly use similar tools to locate Internet-connected IoT devices. In fact, once a device is identified, hacking is not even required in many cases – for example, if default and maintenance passwords are in-use, the attacker’s job is easy as they just flip a switch to exploit.
Attack Surface Assessments and Vulnerability Scanning can show you the internet-connected software, devices and systems that are open to be exploited right now. Easy options to gain this crucial knowledge are available.
Get your Stuff Off Search (S.O.S.)
The Cybersecurity & Infrastructure Security Agency (CISA) has many great free tools and services, particularly in this area.
- S.O.S. – Get your Stuff Off Search. Gives you both How-to instructions and links to tools like Shodan, Censys and Thingful that enable you to see what is visible to anyone on web-based search platforms.
Faction Attack Surface Threat and Vulnerability Assessments
If you don’t have the staff or time to do this yourself, Faction has partnered with the Mobile Intelligence Alliance, a US 501(c)(3) non-profit organization focused on reducing cyber threats to Internet users, to provide independent services in this area. We use the same tools together with expertise, additional technologies and databases developed over decades for a flat fee of $500.00. You can get started on that right now here:
2. Prioritize What Is Critical and Get It Off the Internet
OK, so now you can see what attackers can see. If you are like most companies, it is probably a pretty eye-opening and frightening revelation! But the good news is that not all software, systems and devices are equal. Some are critical to your operations, production and safety of your customers and users and some are not. So, just ask yourself this simple question:
- What software, devices and systems will shut down my business if they are ransomwared or sabotaged?
That’s clearly what you want to focus on first! For this, getting your ‘Stuff Off Search’ is good, but not enough. If it is still connected to the Internet – or connected to another device that is – it can still be attacked. Often, this will happened through back doors and devices you never thought of (see below) that then are the gateway to other parts of your network and software applications. But at the same time, these systems of software, PCs and devices need to be connected to each other and often to Cloud servers that run them. So, what can you do about that?
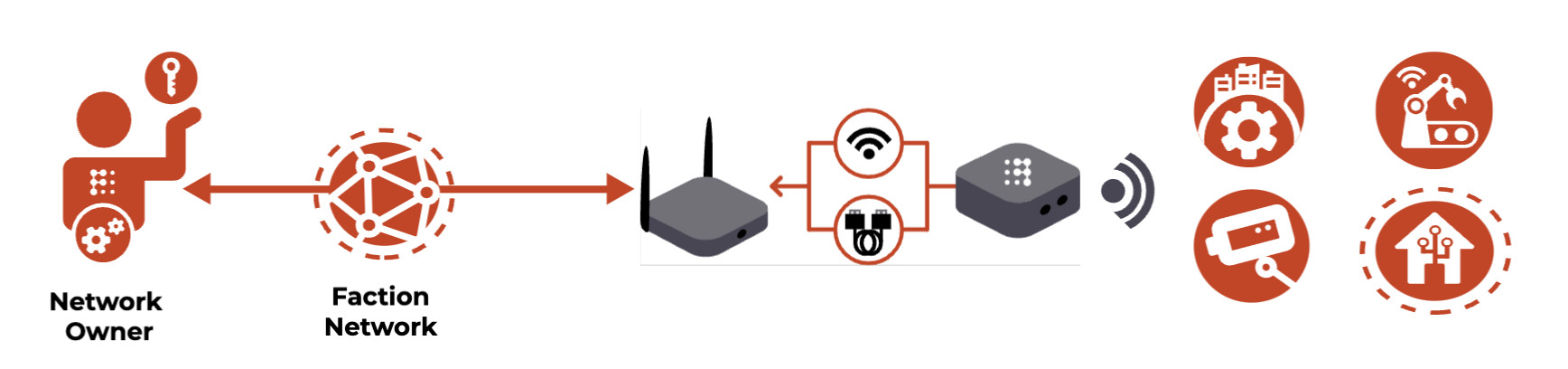
Implement a Faction Virtual Private Circuit
With a Faction Virtual Private Circuit you can take all these OFF the Internet and into your private Faction Network where only the users and devices that you personally invite and authorize can see or access it. This can include:
- computers – whether they are workstations, PC, laptops, smartphones;
- smart, dumb and legacy devices and smart machines – the ones you can’t protect otherwise; and
- cloud servers they need to connect to.
They can all connect and talk to each other, but NOBODY outside of your organization can see of connect to them.
3. Fix known security flaws in your software
OK, so the first two steps will help you to secure the stuff that would threaten to kill your business if attacked. But these next 3 are also important to address the threats to the broader circle of operations of your business.
Always keep in mind that any computing device (PC, laptop, smartphone, etc.) that you add into your Virtual Private Circuit can then be an inside point of attack if it is compromised. Our recommendation is simply do not allow those devices to connect to anything outside. The cost of a few extra PCs and laptops pales in comparison to the cost of a catastrophic attack, and truly shielding your vital systems will reduce your cyber insurance costs.
That said, good ‘cyber hygiene’ is a basic part of maintaining the health of your business. CISA maintains a tremendously useful resource for this:
where you can check for alerts about known and active exploits of software that may be in use right now by your organization. Who else reads these? Attackers! And where they go next – to scanners to zero in on exactly who to attack. Do you get the. picture? if listed, you need to update the software to the latest version according to the vendor’s instructions immediately.
But most people and smaller organizations don’t have time for that – and IT staff or services to do this are expensive. That’s why we put together this handy tool:
We are also working on an AI Bot that will enable you to quickly build a profile of the software and devices you are using, and get an instant read-outs of any current known vulnerabilities. We will also offer the option to subscribe to alerts that will be combined with a private monitoring tool to keep your attack surface at ZERO.
What About When You CAN’T Fix Them?
There are many different situations were this is the case, but two of the most common are:
- legacy computers, smart machines and devices that have are too old to upgrade to newer OSs but vital to your operations or production line; or
- a new exploit in the KEV catalogue that has no current “mitigation” (i.e. there is not a fix yet).
That’s where Faction Pods come in. You simply connect the devices to a Pod – which is a normal WiFi router – and they are now in your Faction Virtual Private Circuit.
4. Implement multifactor authentication (MFA) – or Beyond
Your password isn’t protecting you the way you think it is. It is often trivial for computers to guess passwords, and phishing is the direct cause of most breaches of SMMs. Even if your organization consistently enforces complex passwords – or use of password managers – unfortunately malicious cyber actors still have ways to get past your password. And once they’re in your accounts and networks, the impacts on your business can be catastrophic.
Multifactor authentication (MFA) can make you much more secure. This is a layered approach to securing your online accounts, requiring you provide a combination of two or more authenticators to verify your identity. Taking the extra step beyond just a password can protect your business, bank accounts, data and critical equipment and production lines from hackers. There are many different options and tools – usually readily available and just need to be turned on.
But Don’t Trust Your Critical Devices to MFA
However, we recommend that when it comes to your most critical equipment and networks – the ones that will stop your business cold if they are ransomwared or sabotaged – even MFA can be defeated fairly easily if you are targeted. Why? Because they are cloud-based, and everything in the Cloud can be compromised.
That’s why Faction Virtual Private Circuits use no credentials or external authentication servers whatsoever. You generate your private network with encryption keys created on your own endpoint devices (PC, Laptop, Smartphone, etc.) and share those keys directly to the devices you want to protect. Once added to the network, they are invisible and inaccessible to the Internet.
5. Halt These Other Bad Practices
The list of bad practices – or let’s be honest, stupid things – that people do with software and equipment that is connected to the Internet is a long one! We are compiling a list and primer to help, but if you focus on these first – which tend to be overlooked or not even understood as threats – you will go a long way to reducing your risk of a catastrophic attack. And again, if you don’t have the money or resources to address the right now, you can get all of these device OFF the Internet and into a Faction Virtual Private Circuit with Faction Pods in literally minutes.
- Unsupported (or end-of-life) software
- Old PCs, servers, smart machines which are no longer supported – and thus have no fixes or upgrades for critical vulnerabilities – are more than just a drag on your productivity. They can be the direct open door for attackers.
- Unsecured Security Cameras
- This is not just about your “privacy.” Security cameras are actually the perfect device for malicious actors to attack and hide inside your network – and cover all their activities as well!
- Unsecured Home and Office WiFi Routers
- The recent operation by the FBI to take down a botnet of hundreds of U.S.-based small office/home office (SOHO) routers hijacked by People’s Republic of China (PRC) state-sponsored hackers is just the most recent in a long list.
- Unsecured Printers
- So, your wonderful smart printer connects to the Internet so it can order new ink and paper for you. Guess what, anybody on the Internet with the right tools can find and connect to it!
- Unsecured UPS (Uninterruptible Power Supply)
- Like everything else that has gotten ‘smart’, these devices have all been getting connected to the Internet too – and then attacked! This recent CISA alert on just one model is an example. The convenience and efficiency is important, but once again, a backdoor is opened.
You Have The Power to Do This. We Can Help.
There is always more that can be done, but each one of these steps will have a major and direct impact on radically reducing your attack surface – and thus catastrophic risks to your business. If you implement a Faction Virtual Private Circuit in the recommended way, then you can eliminate all Internet-based threats to your most critical stuff. None of this requires a lot of IT support, or much money, and all can be implemented in a matter of weeks.
Faction Networks can work with you directly or work with your MSP to help get this done. Hopefully, some steps – and others – are already underway. But whatever your status and resource level, we can help you to secure the most critical stuff that makes your business go.










